Introduction
As Azure Logic Apps continues to be one of the go-to tools for integrations in Azure environments. Security is becoming an increasingly pressing matter when conducting integrations, making it a top priority. A great addition to this was introduced to public June 2021. The possibility to integrate Azure Logic Apps properly into a Virtual Network . Virtual Network integration is possible only with Standard Logic App.
The Problem
If you are testing this functionality, which is part of standard Logic Apps (not consumption). You will be using most likely Azure Portal to create and configure resources. Using Azure Portal to do this creates an issue.
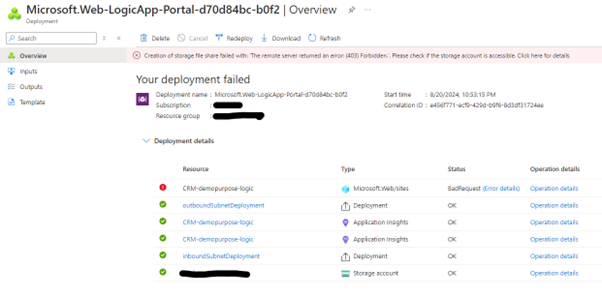
Creation of storage file share failed with: 'The remote server returned an error: (403) Forbidden.'. Please check if the storage account is accessible. (Target: /subscriptions/guid/resourceGroups/RG-name/providers/Microsoft.Web/sites/CRM-demopurpose-logic)
When first facing this issue, I remember doing the deployment multiple times and wondering what was going on. Do not waste time on that, instead keep on reading.
The Solution
The issue here is that the targeted storage account does not allow public access, and it just is not possible to deploy a standard Azure Logic App connected to it via the portal . The workaround is to deploy the resources in a specific order to succeed. Resources need to be deployed with an ARM template , a Bicep script, a Terraform script or such. I found help from this Azure Integration Services Blog: Deploying Standard Logic App to Storage Account behind Firewall using Service or Private Endpoints.
The ARM template, which I used to create the following resources in the correct order:
- Storage account, which denies the public traffic
- Virtual Network and Subnets
- Private DNS Zones and Private Endpoints for blob, file, queue and table services (https://learn.microsoft.com/fi-fi/azure/storage/common/storage-private-endpoints)
- File Share
- App Service Plan (hosting)
- Standard Logic App
- Sets network config with the Virtual Network integration to connect storage account on private endpoints
I used this template as a basis to create my ARM template. As pictures always tell more here you are:
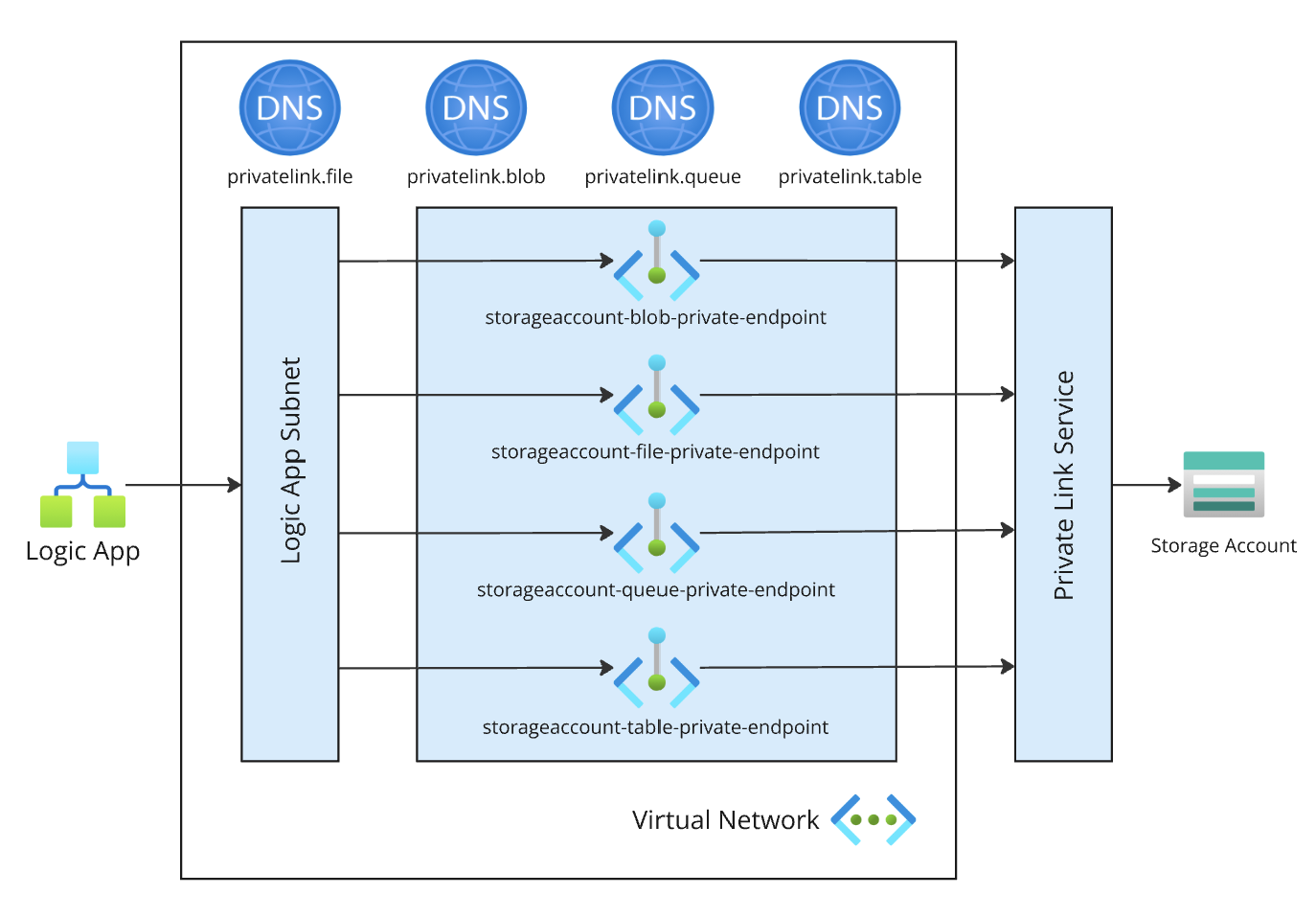
Step-by-step introduction on how to run the ARM template
Application Insights needs to be deployed beforehand as the template does not deploy it.
1. Type to Azure Portal’s search “deploy custom template” and click on found service “Deploy a custom template”
2. Select “Build your own template in the editor”. We can use this feature to upload the provided custom ARM template.
3. Click “Load file” and search for the downloaded custom ARM template (Standard-LogicApp-ARM-template.json).
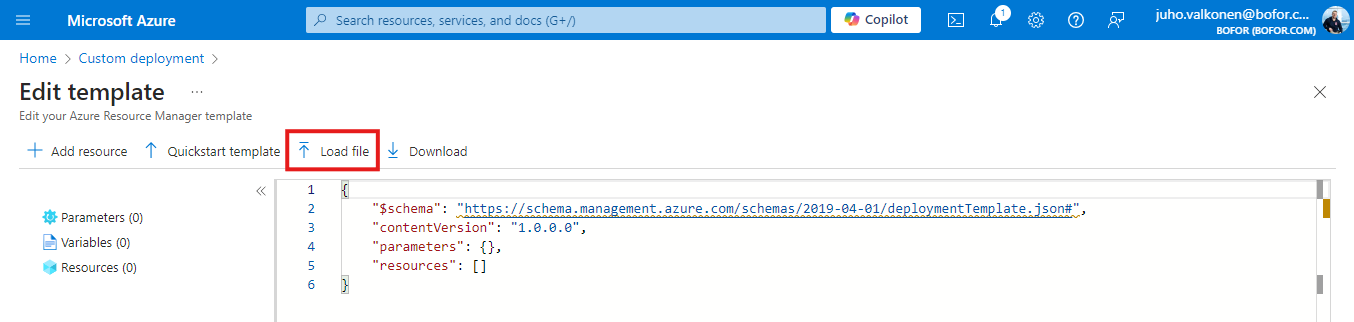
4. Template loads to portal, and you should see 29 parameters and 22 resources on left side navigation. Select “Save”.
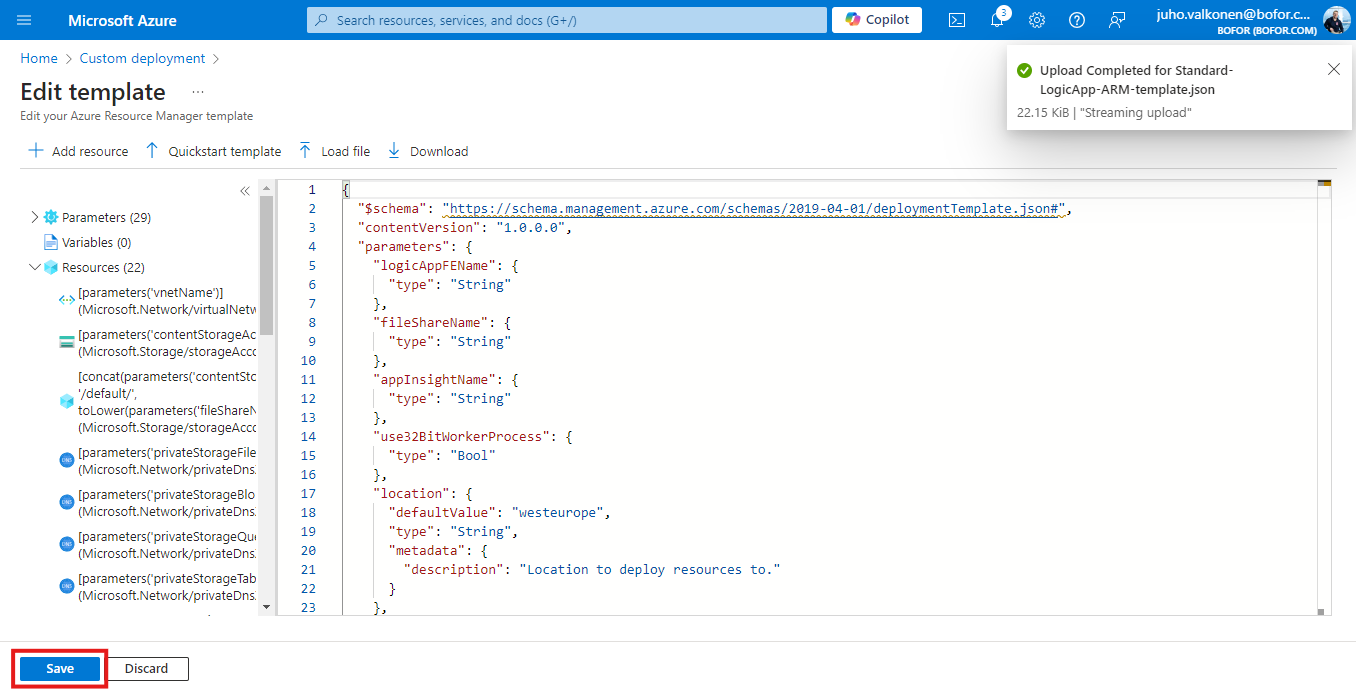
5. There are some predefined example values for some of the parameters. You should go through them all and set them according to your needs. Below is list of them and a short[AS1] description.
| Parameter | Example value | Description |
| Logic App FE Name | Name of the standard Logic App to be deployed. | |
| File Share Name | File Share of the standard Logic App. | |
| App Insight Name | Application Insights where the standard Logic App will be connected to. | |
| Use32Bit Worker Process | true | Standard Logic Apps worker process bits. |
| Location | westeurope | Location to deploy resources to. |
| Hosting Plan FE Name | Standard Logic App’s App Service plan name. | |
| Content Storage Account Name | Storage account to be created. | |
| Sku | WorkflowStandard | App Service Plan’s tier. |
| Sku Code | WS1 | App Service Plan’s pricing. https://learn.microsoft.com/en-us/azure/logic-apps/logic-apps-pricing#standard-pricing |
| Worker Size | 3 | App Service Plan’s worker size |
| Worker Size Id | 3 | App Service Plan’s worker size id |
| Number Of Workers | 1 | App Service Plan’s number of workers |
| Vnet Name | vnetName | Name of the VNET that the Function App and Storage account will communicate over. |
| Subnet Name | VNET subnet name. | |
| Virtual Network Address Prefix | 10.x.x.x/24 | VNET address space. |
| Function Subnet Address Prefix | 0.x.x.x/26 | Function App's subnet address range. |
| Private Endpoint Subnet Address Prefix | 0.x.x.x/26 | Storage account's private endpoint's subnet address range. |
| Private Storage File Dns Zone Name | privatelink.file | Private DNS Zone for Azure File storage |
| Private Storage Blob Dns Zone Name | privatelink.blob | Private DNS Zone for Azure Blob storage |
| Private Storage Queue Dns Zone Name | privatelink.queue | Private DNS Zone for Azure Queue storage |
| Private Storage Table Dns Zone Name | privatelink.table | Private DNS Zone for Azure Table storage |
| Private Endpoint File Storage Name | storageaccount-file-private-endpoint | Private endpoint for Azure File storage |
| Private Endpoint Blob Storage Name | storageaccount-blob-private-endpoint | Private endpoint for Azure Blob storage |
| Private Endpoint Queue Storage Name | storageaccount-queue-private-endpoint | Private endpoint for Azure Queue storage |
| Private Endpoint Table Storage Name | storageaccount-table-private-endpoint | Private endpoint for Azure Table storage |
| Virtual Network Links Suffix File Storage Name | privatelink.file-link | Virtual Network Link for Azure File storage |
| Virtual Network Links Suffix Blob Storage Name | privatelink.blob-link | Virtual Network Link for Azure Blob storage |
| Virtual Network Links Suffix Queue Storage Name | privatelink.queue-link | Virtual Network Link for Azure Queue storage |
| Virtual Network Links Suffix Table Storage Name | privatelink.table-link | Virtual Network Link for Azure Table storage |
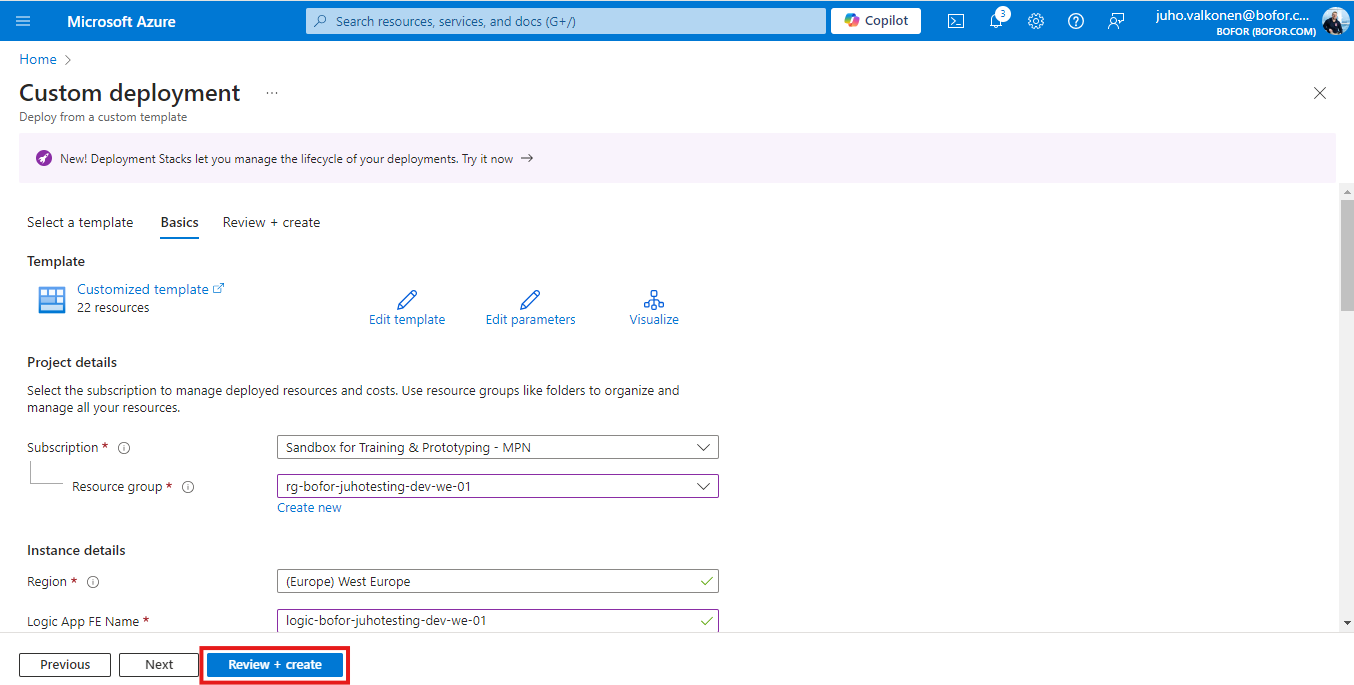
After giving all the parameters, select “Review + create”
6. Select “Create” and start the deployment process.
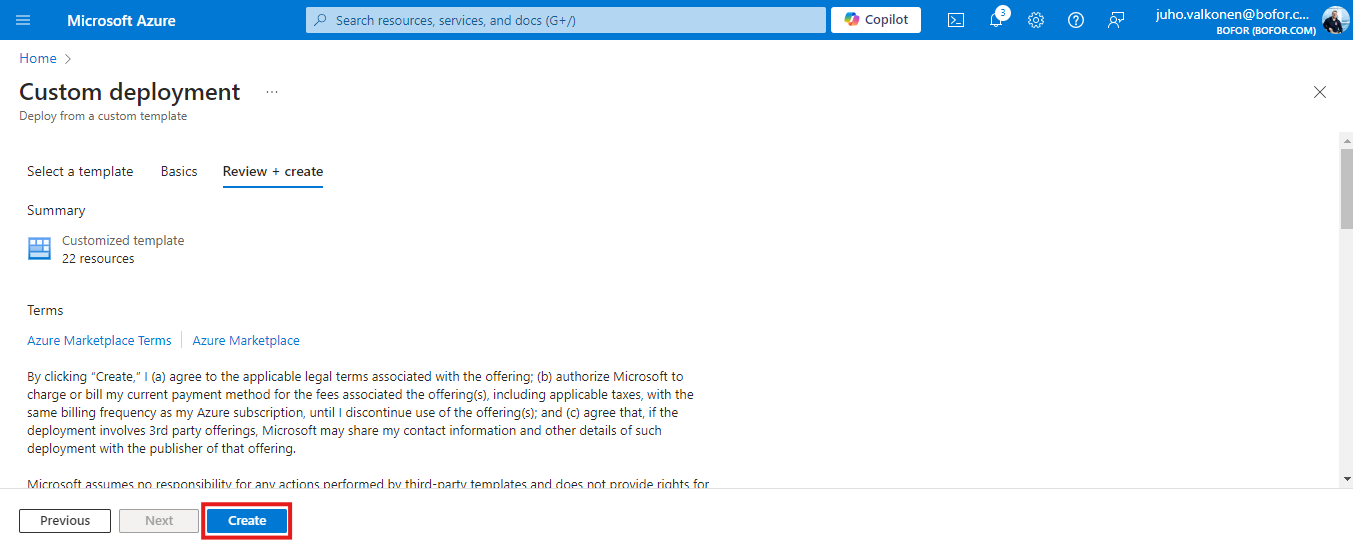
7. *Fireworks

Wrapping It Up
Congratulations! If you've followed our guide successfully, you should now have a secure standard Logic App up and running in Azure. Next, you can begin adding workflows and logic to your app. At Bofor, we frequently use standard Logic Apps to integrate Dynamics 365 or Power Platform with other systems. This might be your goal too! Keep an eye out for more tips on Azure, Dynamics 365, and Power Platform.
Liked this post? Follow Bofor on LinkedIn to get the latest updates.
Contact us to learn more about Bofor and what we can do for you.

